Why the US Cloud Act is a problem and risk for Europe and the rest of the world: a law with far -reaching consequences
Xpert pre-release
Language selection 📢
Published on: April 16, 2025 / update from: April 16, 2025 - Author: Konrad Wolfenstein

Why the US Cloud Act is a problem and risk for Europe and the rest of the world: a law with far -reaching consequences - picture: xpert.digital
How the cloud act undermines confidence in US technology (reading time: 46 min / no advertising / no paywall)
Why the US Cloud Act is a problem and risk for Europe and the rest of the world: a law with far -reaching consequences
This article analyzes the US Clarifying Lawful Overseas Use of Data (Cloud) Act from 2018 and its extensive consequences for global data protection, data sovereignty and international cooperation. The Cloud Act authorities authorizes the publication of data from US communication and cloud service providers that are in possession, care or control, regardless of the physical location of the data-including outside the USA. This extraterritorial range collides fundamentally with data protection regimes such as the General Data Protection Regulation (GDPR) of the European Union, in particular with its rules for international data transfers (Art. 48 GDPR).
The analysis shows that the cloud act creates considerable legal uncertainty for globally operating companies that face contradictory legal requirements. He undermines the trust in US technology providers and established mechanisms for data transfer, a problem that was tightened by the Schrems II judgment of the European Court of Justice. In addition to Europe, the law carries risks of state surveillance, economic espionage and conflicts with local legal systems worldwide.
The global dependence on the large US cloud providers (AWS, Microsoft Azure, Google Cloud) is immense, especially in North America and Europe. At the same time, countries such as China and Russia are developing sealed -off digital ecosystems with strong local providers and strict regulation, which reduces their dependency. Other nations and regions, including the EU with initiatives such as GAIA-X and the Data Act, pursue different strategies for risk reduction, which range from data localization laws to the promotion of local alternatives to negotiations to bilateral agreements with the USA.
Despite the legitimate need to accelerate the cross -border law enforcement - a core concern of the cloud act in view of the slowness traditional legal assistance procedure - the law from the perspective of many critics solves the balancing act between effective crime fighting and the protection of fundamental rights and national sovereignty. The report concludes with recommendations for action for companies and political decision -makers to navigate this complex landscape.
Suitable for:
- Depending on the US cloud? Germany's struggle for the cloud: How to compete with AWS (Amazon) and Azure (Microsoft)
The US cloud act and its effects on European data sovereignty
The advancing digitization and the associated shift of data processing and storage to the cloud infrastructures of global providers have changed fundamentally how companies and public administrations act. In particular, the services of the great US Hyperscaler-Amazon Web Services (AWS), Microsoft Azure and Google Cloud Platform (GCP)-have become an integral part of the digital infrastructure of many countries. This development harbors enormous efficiency and innovation potential, but at the same time creates new and complex challenges for data protection, data security and the maintenance of national sovereignty.
A significant tightening of this problem was carried out by adopting the US Clarifying LawFul Overseas Use of Data (Cloud) Act in March 2018. This US Federal Act admits American law enforcement and investigative authorities to access extensive powers that are stored and managed by US companies or companies under US lawsuit. The core problem lies in the explicit extraterritorial reach of the law: US authorities can request the publication of data, even if they are on servers outside the United States.
This legal regulation leads to direct and fundamental conflicts with established data protection regimes of other countries, especially the General Data Protection Regulation (GDPR) of the European Union. The possibility of access by US authorities with the bypass of international legal assistance procedures and potentially without compliance with the strict European data protection standards stirs up significant concerns about state surveillance, economic espionage and the hollowing out digital sovereignty. The cloud act is therefore widely considered problematic and as a risk for companies and citizens not only in Europe, but worldwide.
This article pursues the goal of providing a comprehensive and well -founded analysis of the US Cloud Act and its global effects. He analyzes the core mechanisms of the law and its extraterritorial dimension. A special focus is on the detailed examination of the potential for conflict with the EU GDPR and the resulting implications for the European data sovereignty, also in the light of the case law of the European Court of Justice (ECJ), in particular the Schrems II judgment. In addition, the risks and potential negative consequences for countries outside of Europe are examined. The report maps the global landscape of the dependence on US cloud providers, identifies regions with high and low dependency and compares the strategies that pursue different countries to manage the challenges created by the cloud act.
The structure of the article follows this objective: After this introduction, the core provisions and the extraterritorial reach of the cloud act are explained in detail in the second chapter. The third chapter is devoted to the conflict zone between the cloud act, the GDPR and European data sovereignty. Chapter four examines the global risks and implications outside of Europe. The fifth chapter maps the global dependence on US cloud providers, while the sixth chapter compares national strategies and reactions to the cloud act. A synthesis of the results and a conclusion form the seventh chapter, followed by recommendations for action in the eighth chapter.
The US Cloud Act: core determinations and extraterritorial reach
The Clarifying LawFul Overseas Use of Data (Cloud) Act represents significant legislation in the area of cross-border data access by US authorities. In order to fully understand its effects, a precise consideration of its legal foundations, its functioning and in particular its extraterritorial claims is indispensable.
Legal foundations and functionality
The cloud act was issued on March 23, 2018 as part of a comprehensive budgetary law (Consolidated Appropriations Act, 2018, Public Law 115-141, Division V) and came into force immediately. It does not represent a completely new legal basis, but changes primarily existing laws, in particular the Stored Communications Act (SCA) from 1986, which is part of the Electronic Communications Privacy Act (ECPA). The SCA regulates the conditions under which US authorities can access stored electronic communication data that is held by service providers.
The core of the cloud act, codifies in 18 USC § 2713 and § 2523, obliges providers of “Electronic Communication Services” (ECS) and “Remote Computing Services” (RCS), which are subject to the Jurisdiction of the United States, to comply with orders for backup or to publish electronic communication and from Metadata or other information about customers or subscribers. This obligation applies to data that is in “possession, custody or under control” (“Possession, Custody, Or Control”) of the provider. The US Jurisdiction can also record providers who do not have their headquarters in the USA, but, for example, through business relationships, a branch in the USA or contracts with US customers have a sufficient connection to the United States.
The crucial clarification that the cloud act brings is that this obligation to hand it into the data regardless of whether the data in question is stored inside or outside the United States (“Regardless of Whether Such Communication, Record, or Other Information is located within the united states”).
The trigger for this legislation was decisive for the legal dispute United States v. Microsoft Corp. (often referred to as “Microsoft Ireland Case”). In this case, Microsoft refused to hand over emails to a customer's FBI who were stored on a server in Ireland on the grounds that US wars had no extraterritorial effect and that the SCA does not apply to data outside the USA. The case reached the Supreme Court, but became no longer (“Moot”) by adopting the cloud act, since it decided the legal question in the sense of the government.
It is important to emphasize that, according to the US government and supporting organizations, the cloud act is not a license for mass surveillance or arbitrary data access. Access arrangements (typically warrants based on “probable causes”, or subpoenas) must continue to meet the rule of law of US law, be specific and are subject to judicial control. They are limited to data that could be relevant in connection with specific criminal investigations (“Serious Crime, including Terrorism”). Furthermore, the cloud act explicitly creates no obligation for providers to decipher data if they only have them in encrypted form and do not control the keys.
Extraterritorial application and jurisdiction claim
The central and most controversial innovation of the cloud act is the statutory anchoring of the extraterritorial reach of US access arrangements. The law makes it clear that there is an obligation to surrender data for providers under US Jurisdiction regardless of the physical location of the data.
This position is based on the established legal principle that a state that is subordinate to its jurisdiction can oblige information to surrender information that are under its control, even if this information is stored abroad. The cloud act specifically codes this principle for electronic communication data in the context of the SCA.
It is precisely this unilateral claim to extraterritorial access is the main source of international concern and legal conflicts, especially in relation to the European Union and its General Data Protection Regulation (GDPR). It is perceived as an interference with the sovereignty of other countries and as a potential circumvention of established international legal assistance procedures.
Executive agreements as an alternative to legal assistance agreements
In addition to clarifying the extraterritorial reach of US arrangements, the cloud act introduces a second important mechanism: it authorizes the US executive (president or government), bilateral agreements, so-called “Executive Agreements”, with “qualified” foreign governments.
The declared goal of this agreement is to accelerate and make the cross -border data access for criminal prosecution for serious crimes (“Serious Crime, including Terrorism”). They should offer an alternative or addition to the traditional legal assistance agreements (Mutual Legal Assistance Treaties, Mlats), whose procedures are often criticized as too slow and bureaucratic in order to keep up with the speed of digital crime.
The core mechanism of these executive agreeing is to eliminate legal obstacles (“Conflicts of Law” or “Legal Restrictions”), which could prevent providers to follow legitimate arrangements of the partner country. Specifically, such an agreement would, for example, allow a US provider to meet an order from the United Kingdom directly without violating US law (e.g. SCA restrictions on disclosure), and vice versa. The authorities of each country could thus use their own national procedures to request data from the provider in the other country.
However, the United States can only conclude such agreements with states that are considered “qualified”. The prerequisite for this is a certification by the US Attorney General (Minister of Justice) and the Secretary of State (Foreign Minister) compared to the congress that the partner country in question has robust material and procedural protective mechanisms for privacy and bourgeois freedom. The partner country must respect the rule of law, non -discrimination and data protection.
So far, the United States has completed such executive agreements with the United Kingdom (signed in 2019, in force since October 2022) and Australia (signed December 2021). Negotiations with the European Union were announced in 2019 and are underway, but are difficult due to the complex legal situation (GDPR, Schrems II) and the participation of 27 Member States.
Important protection measures for these agreements are provided in the cloud act itself: Orders that are under such an agreement must not target US people (citizens or people with a constant stay) or people who are in the United States. You must be specific (e.g. targeting a specific person, an account) and is subject to independent review or supervision (e.g. by a dish).
Announcement options for providers
The cloud act explicitly provides for a mechanism with which providers can contest US access arrangements under certain conditions (so-called "Motion to quash or modify"). This right exists if the provider “believes reasonably” (“Reasonably Believes”) that two cumulative conditions are met:
- The affected customer or subscriber is not a US person and has no residence in the United States.
- The required disclosure would create a “material risk” that the provider violates the laws of a “qualified foreign government”. A “qualified foreign government” is one with which the United States has completed an executive aggreement as part of the Cloud Act.
If the provider submits such a contestation, the responsible US court can change or cancel the order. However, this only happens if the court determines that (a) the disclosure would actually violate the law of the qualified foreign state (b) the granting of the contesting “the interests of the judiciary” (“Interests of Justice”) serves, and (c) the interests of the judiciary require this, taking into account the “total of circumstances” (“Totality of the CircumStances”).
For the assessment of what the “interests of the judiciary” require, the law lists specific factors that the court must weigh up (“community analysis”). This includes, among other things, the interests of the United States and the foreign government, the probability and type of punishment that would threaten the provider abroad, the connections of the person concerned and the provider to the USA and abroad, the importance of the information for the determination and availability of alternative ways to procurement.
However, this legal regulation raises questions about their practical effectiveness. The focus of the explicit reason for contestation on legal conflicts with qualified foreign governments (i.e. those with Executive Agreement) could weaken the position of providers that want to rely on laws of countries without such an agreement, such as the EU GDPR in the current state without EU-US agreements. It remains to be used to rely on general principles of international courtesy and balancing of interests (“Common Law Commit”), but the specific legal mechanism is closer. This could tempt US courts to measure conflicts with laws of non-agreement states less weight or to consider the contesting process as less clearly defined.
In addition, the practical relevance of the possibility of contestation is generally limited. The burden of proof lies with the provider, which must prove that he "believes reasonably" that the conditions are fulfilled. Even if a legal conflict is demonstrated, the court can cancel the order, but it does not have to. The decision is based on a weighing of indefinite legal terms such as “interests of the judiciary” and “entirety of circumstances”, which give the court a wide range of discretion. There is a risk that US interests, especially in law enforcement or security issues, are systematically weighted higher than foreign data protection interests, especially if there is no bilateral agreement that formally recognizes these interests. The European Data Protection Committee (EDSA) therefore looks at this mechanism skeptical and emphasizes that it is only a way to contest, does not offer any obligation, and therefore not sufficient security for the rights of EU citizens.
Suitable for:
- The digital dependence on the USA: cloud dominance, distorted trading balance sheets and lock-in effects
Conflict zone: Cloud Act vs. EU GDPR and data sovereignty
The extraterritorial reach of the US Cloud Act and the associated access powers for US authorities lead to considerable tensions and direct legal conflicts with the data protection regime of the European Union, in particular the General Data Protection Regulation (GDPR). These conflicts concern core principles of EU data protection law and raise fundamental questions about data sovereignty.
Direct collision with the GDPR (Art. 6, Art. 48)
The fundamental conflict results from the fact that the Cloud Act Authorities enables the transmission of data-including personal data from EU citizens-from the EU to the USA, without necessarily based on one of the legal basis for data processing or international data transfer provided in the GDPR.
The conflict with Article 48 GDPR is particularly relevant ('transmission or disclosures that are not permitted under Union law'). This article stipulates that decisions of courts or administrative authorities of a third country who oblige a responsible or order processor to transmit or disclose personal data are only recognized or enforceable if they are based on international law - such as a legal assistance (MLAT) - which is in force between the requesting third country (here the USA) and the Union or a Member State. An arrangement based solely on the cloud act without being legitimized by such an international agreement does not meet this condition. From the GDPR's point of view, it is not a valid legal basis for the transfer.
In addition, there is no such transmission to a valid legal basis in accordance with Article 6 GDPR, which defines the conditions for the legality of processing (including transmission) of personal data. The European Data Protection Committee (EDSA) and the European Data Protection Officer (EDSB) made it clear in their joint evaluation that the usual legal bases do not apply here:
- Art. 6 (1) (c) GDPR (fulfillment of a legal obligation): This legal basis is not applicable because the “legal obligation” comes from the cloud act, that is, from the law of a third state, and not from the law or the right of a Member State, as required by Art. 6 (3) GDPR. There would only be an exception if the US arrangement was anchored in EU law by an MLAT.
- Art. 6 (1) (e) GDPR (perception of a task in the public interest): This legal basis also rules out, since the task (here the compliance of the US arrangement) is not set in Union law or in the right of a Member State.
- Art. 6 (1) (f) GDPR (maintaining legitimate interests): A provider could have a legitimate interest in complying with a cloud act order to avoid sanctions under US law. However, according to EDSA/EDSB, this interest is regularly predicted by the interests or fundamental rights and fundamental freedoms of the data subjects (protection of their data). The authorities argue that those affected could otherwise be robbed of their protection according to the EU fundamental rights charta (in particular the right to effective legal remedies, Art. 47).
- Art. 6 (1) (d) GDPR (protection of vital interests): This legal basis could theoretically be applicable in very narrowly limited exceptional cases, for example if the data is required to avert an immediate danger to the body and life of a person. However, it does not offer a basis for routine data expenditure in the context of law enforcement measures.
This collision of the legal norms creates an indissoluble conflict for providers that are subject to both the US Jurisdiction (and thus the cloud act) and EU legislation (GDPR). Follow a cloud act arrangement without a MLAT base, violate the GDPR and risk high fines (up to 4% of the global annual sales) and civil law lawsuit. If you refuse to publish, citing the GDPR, risk sanctions under US law.
Evaluation by the EDSA/EDSB and legal uncertainty
The European data protection supervisory authorities, coordinated in the EDSA and the EDSB, have made a clear position on this conflict situation. In their joint legal assessment of July 2019, they came to the conclusion that the cloud act as such is not a sufficient legal basis according to the GDPR for the transmission of personal data to the USA.
They emphasize that providers who are subject to EU law may not transmit personal data to US authorities solely on the basis of a direct arrangement according to the cloud act. Such a transmission is only permitted if it is based on a recognized international agreement, typically based on the EU-US Mlat or a bilateral Mlat between a Member State and the USA. The MLAT process guarantees the necessary rule of law and the integration of the judicial authorities of the requested state.
The possibility for providers intended in the cloud act to contest an arrangement (“motion to quash”) is assessed by EDSA and EDSB as an inadequate protective mechanism. They point out that this is only an option for the provider, not an obligation, and that the outcome of such a procedure before a US court is uncertain and does not guarantee the protection of EU citizens according to EU standards.
This clear attitude of the relevant European data protection authorities tightens legal uncertainty for companies that use or offer US cloud services. You must be aware of the fact that the use of such services is not potentially not-compliant if the provider cannot guarantee that he does not publish data on the basis of a cloud act arrangement while violating the GDPR.
Implications of Schrems II and US monitoring laws
The problem of the cloud act must be seen in the context of the broader debate about data transfer to the USA and the surveillance laws there, which has achieved a new dimension from the Schrems II judgment of the ECJ of July 16, 2020.
In this judgment, the ECJ declared the EU-US Privacy Shield Agreement invalid. The main reason for this was the far-reaching powers of the US intelligence services (especially according to Section 702 of the Foreign Intelligence Surveillance Act-FISA-and Executive Order 12333) to access personal data from EU citizens that are transmitted to the USA. The ECJ found that these access options do not meet the requirements of EU fundamental rights charta in need and proportionality and that EU citizens are not available to effective legal protection against such access in the USA.
Although the cloud act formally is an instrument of law enforcement and not the intelligence surveillance, it increases the concerns raised by Schrems II. It establishes another legal mechanism for extraterritorial access to data by US authorities. From a European perspective, this mechanism (unless it is not based on a MLAT or a future, as an adequate agreement) is also missing the necessary rule of law in EU law (Art. 48 GDPR). The combination of access rights from surveillance laws (FISA 702, EO 12333) and the cloud act (law enforcement) creates an overall picture of far-reaching state access options for data that is stored globally by US providers.
This has a direct impact on the use of other transfer mechanisms such as the standard contract clauses (Standard Contractual Clauses, SCCS). The Schrems II judgment obliges data exporters to check when using SCCs for transfers to third countries such as the USA in individual cases whether the right and practice of the target country ensure a level of protection that is "essentially equal" in the EU. If not, additional measures (supplementary measures) must be taken to close any gaps in protection. The existence of laws such as FISA Section 702 and the cloud act makes it extremely difficult for companies to prove that US law offers such an equivalent level of protection. This makes the right-wing use of US cloud services significantly more difficult for the processing of personal data from the EU. The cloud act looks like an amplifier of the Schrems II problem, since it expands the spectrum of statutory US access options and further undermines the argument for “significant equivalence” of the protection level.
Hoast of European data sovereignty and loss of trust
In addition to the purely legal conflicts, the cloud act is widely perceived as a threat to the digital sovereignty of Europe. Data sovereignty describes the right and ability of states, organizations or individuals to control their data, especially where it can be stored, how it can process and who can access it. The cloud act undermines this principle by allowing a foreign power (the United States) to potentially access data that is stored on European territory or come from European citizens and companies, provided that this data is managed by a provider under US legal.
The possibility of such access that may be without compliance with European procedures (such as MLATS) and without the knowledge or notification of the data or companies that may be given or notify leads to a significant loss of trust in US technology providers. This distrust not only affects the protection of personal data within the meaning of the GDPR, but also extends to the security of sensitive company data, such as business secrets, research and development data, financial information and intellectual property. The concern of business espionage or the unwanted drainage of competitive information through government access is an essential factor that causes companies to search for alternatives to US providers or to take additional protective measures.
EU answers: Data Act and Gaia-X (status and challenges)
In response to the challenges of digitization and the dominance of non -European technology providers, the European Union launched various initiatives to strengthen digital sovereignty and to define its own European way in dealing with data. Two central building blocks are the Data Act and the Gaia-X initiative.
The EU Data Act, which was published in the Official Journal in December 2023 and will be applicable from September 12, 2025, aims to increase fairness in the data industry and to improve access and use of data, especially industrial data. It is intended to promote innovation and increase the availability of data. Specifically, the data act of users of networked products (e.g. IoT devices, smart machines) gives more control over the data generated by these devices and facilitates the change between different cloud providers, for example by reducing hurdles for changing providers and prohibiting inappropriate contractual clauses. The provisions that protective measures against illegal data transmission requirements of third-country country authorities should also provide relevant in the context of the cloud act and thus strengthen EU data conference.
The Gaia-X initiative, launched in 2019, pursues the ambitious goal of creating a fed, safe and sovereign European data infrastructure. GAIA-X is intended to establish an ecosystem in which data according to European values and standards-transparency, openness, security, interoperability and data sovereignty-can be shared and processed. It is said to offer an alternative to the dominant hyperscalers and reduce the dependence on non -European providers.
However, Gaia-X is still in an early phase of implementation (“Ramp-up phase”) and faces significant challenges. There are first pilot projects and application cases such as Catena-X for the automotive industry or test beds in partner countries such as Japan, but there is still a wide range of market penetration. The hurdles include the technical complexity of the federated approach, ensuring real interoperability between different providers, governance questions within the GAIA-X Association (the sponsoring organization) and slow adoption, especially in highly regulated sectors such as healthcare. There was also criticism that the original vision of a purely European cloud was watered down by the integration of the large US hyperscales in the Gaia-X Association and that the project suffered from excessive bureaucracy. It is currently unlikely that Gaia-X can build a direct competition with AWS, Azure and GCP. Its importance could be more due to framework for standards and trust for specific European data rooms (data spaces).
However, these European initiatives also reveal strategic inconsistency. On the one hand, GAIA-X and the Data Act attempt to reduce the dependence on US providers and to strengthen control over data in Europe. On the other hand, the European Commission negotiates in parallel with the United States about an executive agree as part of the Cloud Act. Such a agreement would, if it occurred, legalize direct data access by US authorities under certain conditions and potentially simplify-i.e. exactly the mechanism that originally triggered the sovereignty concerns. This reflects the EU's dilemma of striving for digital autonomy at the same time and to put the pragmatic cooperation with the USA in criminal prosecution on an efficient basis, without revealing your own high data protection principles (in particular the requirements from the Schrems II judgment and Art. 48 GDPR). The dissolution of this voltage is a central challenge for the future transatlantic data policy.
🎯📊 Integration of an independent and cross-data source-wide AI platform 🤖🌐 for all company matters

Integration of an independent and cross-data source-wide AI platform for all company matters-Image: Xpert.digital
Ki-Gamechanger: The most flexible AI platform-tailor-made solutions that reduce costs, improve their decisions and increase efficiency
Independent AI platform: Integrates all relevant company data sources
- This AI platform interacts with all specific data sources
- From SAP, Microsoft, Jira, Confluence, Salesforce, Zoom, Dropbox and many other data management systems
- Fast AI integration: tailor-made AI solutions for companies in hours or days instead of months
- Flexible infrastructure: cloud-based or hosting in your own data center (Germany, Europe, free choice of location)
- Highest data security: Use in law firms is the safe evidence
- Use across a wide variety of company data sources
- Choice of your own or various AI models (DE, EU, USA, CN)
Challenges that our AI platform solves
- A lack of accuracy of conventional AI solutions
- Data protection and secure management of sensitive data
- High costs and complexity of individual AI development
- Lack of qualified AI
- Integration of AI into existing IT systems
More about it here:
Economic espionage and data protection: Is US technology still trustworthy?
Global risks and implications outside of Europe
The problems raised by the cloud act are not limited to the relationship between the USA and Europe. The law has potentially far -reaching effects on countries and regions worldwide, especially with regard to state monitoring, economic espionage, conflicts with local laws and general trust in global digital infrastructure.
State surveillance and bourgeois freedoms
From the beginning, the cloud act has attracted criticism of civil rights organizations such as the Electronic Frontier Foundation (Eff) and the American Civil Liberties Union (ACLU). One main point of criticism is that the law potentially undermines the protective mechanisms against inappropriate state searches and seizures (anchored in the 4th additional article of the US constitution for US citizens). In particular, the possibility of creating bilateral regulations via Executive Agreements that enable direct data access by foreign authorities to data in the USA and possibly deal with the usual judicial control by US dishes is considered problematic. In addition, those affected by a data request do not necessarily have to be informed about access under the cloud act, which limits the possibilities for the perception of legal remedies.
For people outside the United States, protection from the US constitution is lower anyway. The cloud act makes it easier for the US authorities to access their data stored in US providers, regardless of the location. This stirs up fears worldwide regarding an expansion of state surveillance by the United States. There is concern that the mechanism of the cloud act, in particular the executive agree, could serve as a model for other states, even those with lower rule of law and less pronounced protection of bourgeois freedoms. The parallel to China's National Intelligence Law, which Chinese authorities also granted far -reaching access rights to data from companies, has already been drawn. This could promote global trends towards increased state surveillance and control of digital communication.
Economic espionage and protection of intellectual property
The access powers under the cloud act are not limited to communication content or metadata from private individuals. You can also potentially record highly sensitive company data stored by US cloud providers. This includes business secrets, financial data, customer databases, prototypes, research and development data as well as other intellectual property (intellectual property, IP).
Even if the explained purpose of the cloud act is to combat serious crime, there is a concern that far-reaching access options could be abused, for example for the purposes of business espionage in favor of US companies or to obtain strategic economic advantages. The mere possibility of such access by a foreign government power undermines the trust of companies worldwide into the security and confidentiality of their critical data if they lie with US providers. This risk is a significant disadvantage in the use of US cloud services for many companies, especially in technology-intensive or security-critical industries.
Conflicts with local legal systems
Similar to the case of the EU GDPR, the extraterritorial claim of the Cloud Act can also collide with the data protection laws, confidentiality obligations or other legal provisions of numerous other countries. Global cloud providers, especially those with headquarters or strong presence in the USA, are therefore potentially exposed to a network of contradictory legal obligations.
Examples of countries with their own data protection regimes that are potentially in conflict with the cloud act are numerous:
- Switzerland: The revised federal law on data protection (REVFADP) is strongly based on the GDPR and also contains rules for international data transfers that require adequate protection in the target country.
- Brazil: The Lei Geral de Proteção de Dados Pessoais (LGPD) also has extraterritorial effects and subjects the processing of data to Brazilian citizens Strict rules, including for international transfers.
- India: The Digital Personal Data Protection Act (DPDP Act, often still referenced as PDPB) also contains provisions on data transfers and may provide localization requirements for certain “critical” data.
- China: The Cybersecurity Law (CSL) and the Personal Information Protection Law (Pippl) see strict rules for data security and cross -border transfers and include data localization requirements.
- Russia: Federation Law No. 152 “About personal data” prescribes the storage of personal data from Russian citizens on servers in Russia (data localization).
These examples make it clear that the cloud act is not only a bilateral problem between the USA and the EU, but is also a global challenge for the coherence of international legal systems in the digital space.
Effects on international data transfers and trust in US technology providers
The existence of the cloud act and the associated uncertainties and legal conflicts have a significant impact on international data transfer mechanisms and the general trust in US technology providers.
The law contributes to the erosion of trust in established instruments for transatlantic data traffic, such as the former EU-US privacy Shield or the currently heavily used standard contract clauses (SCCS). As explained in the context of Schrems II, the cloud act complicates that in the United States there is an EU law “essentially equivalent” protection level for personal data.
This forces companies worldwide to re-evaluate the risks when using US cloud services. You have to check whether and how you can ensure compliance with your local data protection laws if you have data transmitted to US providers or have it processed by them. This increasingly leads to the examination of alternative solutions, such as the use of local or regional cloud providers that are not subject to the US Jurisdiction, or to implement additional technical and organizational protective measures (such as end-to-end encryption with their own key management, data pseudonymization or strict data localization for certain data types).
The legal uncertainty created by the cloud act and similar laws of other countries and the resulting protective measures could also increase a tendency towards the “Balkanization” of the Internet. This is an increasing fragmentation of the global digital space along national or regional borders, characterized by stricter data localization requirements, different technical standards and difficult cross -border data flows. The cloud act acts here as an essential driver for this global trend towards more digital sovereignty. By unilateral, by anchoring extraterritorial access to data and thus potentially transferring the legal systems of other states, they provoke counter -reactions. These manifest themselves in the form of data localization laws, the state funding of local cloud ecosystems and the tightening of national data transfers. The cloud act thus accelerates, possibly unintentionally, a development away from an open, globally networked data space to more nationally or regional controlled digital territories.
Suitable for:
Mapping of the global dependence on US cloud providers
In order to be able to assess the scope of the cloud act, an understanding of the global market shares and the resulting dependencies on the large US cloud providers-Amazon Web Services (AWS), Microsoft Azure and Google Cloud Platform (GCP)-is essential. The market dominance of these actors significantly determines how many companies and organizations could potentially affect cloud acts worldwide.
Market shares of the US hyperscalers (AWS, Azure, GCP)
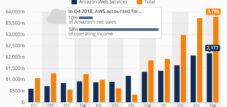
Numerous market analyzes confirm the overwhelming dominance of the three large US hyperscales in the global market for cloud infrastructure services (infrastructure-as-a-service, IAAS and platform-as-a-service, PAAS). Together, AWS, Microsoft Azure and GCP at the end of 2023 and early 2025 (depending on the source and precise definition of the market) controlled a share of around 66% to 70% of global sales in this segment.
The approximate market shares for the fourth quarter 2024 can be summarized as follows (based on data from different sources, exact numbers can vary slightly, but the trend is consistent):
- Amazon Web Services (AWS): approx. 30-33%. AWS is still the clear market leader, whose pioneering role in cloud computing ensures a continued lead. However, there is a slight tendency towards stagnation or even a slight decline in the market share in recent years, while the competition catches up.
- Microsoft Azure: approx. 21-24%. Azure has established itself as a strong number two and has continuous growth, often driven by integration with other Microsoft products and a strong position in the company sector.
- Google Cloud Platform (GCP): approx. 11-12%. GCP is number three and also shows significant growth, albeit from a smaller basis. Google invests strongly in areas such as AI and data analysis to gain market shares.
In addition to these three giants, there are other relevant actors, whose market shares are significantly lower. This includes Alibaba Cloud, which plays a smaller role at about 4% globally, but dominates the cloud market in China. Other providers with global or regional priorities include IBM, Salesforce, Oracle, Tencent Cloud and Huawei Cloud (both strong in China) and specialized providers.
The following table summarizes the estimated global market shares of the leading cloud infrastructure providers (IAAS / PAAS) for the end of 2024 / early 2025 and illustrates the dominance of the US hyprees:
Estimated global cloud market shares (IAAS/PAAS) Q4 2024/early 2025
The current data of the global cloud market for IAAS/PAAS in the fourth quarter of 2024 and at the beginning of 2025 show a clear dominance of the American hyperscales. AWS claims the largest market share with 30 to 33 percent, whereby a stable to slightly declining trend can be observed. Microsoft Azure follows with 21 to 24 percent and lists further growth. Google Cloud Platform (GCP) secures 11 to 12 percent of the market with positive development tendency. The Chinese provider Alibaba Cloud holds a stable global market share of around 4 percent. The other providers, including IBM, Oracle, Tencent and Huawei, share 27 to 34 percent of the market with different development trends. The overall position of the US hyperscaler is remarkable, which together control around 62 to 69 percent of the global cloud market and record slight growth.
These numbers underline the considerable global dependence on the three major US providers. Much of the global cloud infrastructure is therefore potentially subject to the jurisdiction of the cloud act.
Regions/countries with high dependency
The dependence on US cloud providers is geographically different, but very high in many important economic regions:
- North America (especially USA and Canada): As a home of the hyperscaler and with the highest cloud penetration, dependence is naturally greatest here. AWS has a particularly strong market position in the USA. Canada also shows high investments in the cloud and AI, often through US platforms.
- Europe: Despite the concerns regarding GDPR and cloud act, the dependence on AWS, Azure and GCP in Europe is extremely high. Your combined market share on the continent is estimated at over 70%. Interestingly, in some European countries such as the Netherlands (allegedly 67%market share), Poland (49%) and also in Japan (49%), even in Japan (49%), even seems ahead of AWS according to an analysis. Large European economies such as Germany, the United Kingdom and France invest massively in cloud technologies and artificial intelligence, with the US platforms playing a central role. This discrepancy between high market dependency and the political striving for digital sovereignty represents a central area of tension.
- India: The Indian cloud market shows a high growth dynamics and a strong dependence on US providers, whereby the market structure of which in the USA leads: AWS (approx. 52%) before Azure (approx. 35%) and GCP (approx. 13%). At the same time, there is a strong political will for digitization and increasingly efforts to localize data, especially for sensitive data such as financial data. This could promote the growth of local providers in the long term.
- Latin America: Cloud use in countries such as Brazil grows, but is also strongly dominated by global US players. AWS is actively expanding in the region, for example with a new region in Mexico. Local data protection laws such as the Brazilian LGPD and specific data localization requirements, for example in the financial sector, could influence market dynamics, but have so far not been changing the basic dependency.
- Australia: As a technologically highly developed country with a close political and economic bond with the United States, Australia has a high cloud adoption. The existence of a cloud act executive agree between the United States and Australia indicates acceptance of US access mechanisms and suggests a high dependence on US providers.
- Other regions (e.g. Africa, parts of Southeast Asia): The cloud markets are only building up in many developing and emerging countries. Often the global US providers also dominate here due to their scale advantages and their technological advantage. At the same time, the efforts of digital sovereignty and data localization also increase in these regions, as examples from Vietnam or Indonesia show.
Countries with less dependency and alternative ecosystems (China, Russia)
In contrast to the widespread dependence on US hyperscalers, particularly independent digital ecosystems have developed, especially in China and Russia, which are dominated by local providers.
- China: The Chinese cloud market is the second largest in the world, but it is heavily regulated and is difficult to access for foreign providers. The dominance is clearly with domestic technology groups: Alibaba Cloud holds a market share of about 36%, followed by Huawei Cloud with approx. 19% and Tencent Cloud with approx. 15-16% (stand Q2/Q3 2024). US providers such as AWS or Azure only play a subordinate role on the Chinese mainland market. This development is funded by strict state regulation, in particular the cybersecurity law (CSL) and the Personal Information Protection Law (PIPL), which, among other things, prescribe data localization requirements and consider the cross -border data flow. China also pursues its own ambitious strategy in the field of artificial intelligence that builds on the capacities of domestic cloud providers.
- Russia: Similar to China, albeit for other reasons (especially western sanctions and an active state politics to promote digital sovereignty), an increasing decoupling of western technology providers has taken place in Russia. The Russian cloud market is dominated by local providers, above all Yandex Cloud, but also providers such as Sbercloud (now possibly name, for example, in the name, e.g. Cloud.ru), VK Cloud and the state-controlled telecommunications group Rostelecom play an important role. The Russian Data Protection Act (Föderales Law No. 152) stipulates a strict data localization for personal data from Russian citizens, which makes it difficult to use foreign cloud services and promote local providers. Yandex Cloud explicitly advertises with compliance with these local laws to attract international companies that want to work on the Russian market. State programs such as “digital economy of the Russian Federation” and the “Gostech” platform also promote the use of domestic cloud solutions by authorities and companies.
- European Union (potential vs. reality): The EU is in a special situation. On the one hand, there are clear political efforts to reduce the dependence on US providers and to build their own digital sovereignty. Initiatives such as Gaia-X and legislative acts such as the Data Act aim in this direction. There are also a number of European cloud providers (e.g. Ovhcloud, Deutsche Telekom/T-Systems, Ionos). On the other hand, the actual market penetration of the US hyperscales in Europe, as shown above, is extremely high. So far, the European alternatives have not been able to achieve comparable market shares, which is often attributed to scale disadvantages and the technological maturity of the US offers. The EU thus remains a field of high dependence with strong political will.
These examples show that a lower dependence on US hyperscalers is possible, but are mostly based on a combination of strong state regulation, targeted promotion of domestic industries and sometimes also politically motivated market shutdown.
🎯🎯🎯 Benefit from Xpert.Digital's extensive, fivefold expertise in a comprehensive service package | R&D, XR, PR & SEM

AI & XR 3D Rendering Machine: Fivefold expertise from Xpert.Digital in a comprehensive service package, R&D XR, PR & SEM - Image: Xpert.Digital
Xpert.Digital has in-depth knowledge of various industries. This allows us to develop tailor-made strategies that are tailored precisely to the requirements and challenges of your specific market segment. By continually analyzing market trends and following industry developments, we can act with foresight and offer innovative solutions. Through the combination of experience and knowledge, we generate added value and give our customers a decisive competitive advantage.
More about it here:
Digital race for sovereignty: teaching from the cloud act
National strategies and reactions to the cloud act
In view of the challenges that the US Cloud ACT for data protection, sovereignty and legal certainty, states have developed different strategies worldwide to manage the associated risks and protect their interests. These strategies range from regulatory measures to technological approaches to international negotiations.
Comparison of national approaches
Several basic approaches can be observed, which are often combined:
- Data localization: One of the most direct reactions is the introduction of laws that stipulate that certain types of data - often personal data or as critically classified information - must be physically stored and processed physically within the national borders. Prominent examples of this are Russia with the federal law No. 152, China with requirements under the cybersecurity law and Pippl and partly India (especially for payment data). Countries such as Vietnam and Indonesia also pursue such approaches. The motifs are diverse: strengthening national sovereignty and control over data, improvement in national security through difficult access to foreign powers, but also economic protectionism to promote domestic IT industry. Technologically and economically, however, strict data localization is often inefficient because it undermines the advantages of globally distributed cloud architectures (such as scalability, redundancy, cost efficiency) and leads to higher costs for companies. The number of countries with such restrictions has increased significantly in recent years.
- Strengthening your own regulation and international standards: Many countries rely on strengthening their own data protection legislation in order to establish high protective standards and to clearly regulate the conditions for international data transfers. The EU with the GDPR is a pioneer here. Other countries have followed up or modernized their laws, often based on the GDPR, such as Switzerland (Revfadp), Brazil (LGPD), the United Kingdom (UK GDPR) or Canada (Pipeda). The aim is often to be recognized by the EU as a country with a “reasonable level of data protection” in order to facilitate the data flow with Europe. At the same time, these laws serve to protect the rights of one's own citizens and to create a legal framework that can potentially be asserted with laws such as the cloud act in the event of a conflict.
- Promotion of local/regional providers and ecosystems: Another approach is the active industrial policy funding of domestic or regional cloud providers and digital ecosystems in order to create alternatives to the dominant US hyperscalers and to reduce technological dependency. The EU initiative GAIA-X is an example of this, even if your success has so far been limited. In China and Russia, this approach, combined with strong regulation, is more successful and has led to markets dominated by local providers. The challenge is that local providers often do not achieve the same scale effects, the same investment volume or the same global range as the US giants.
- Use of international agreements (Executive Agreements vs. Mlats): States can try to regulate data access as part of law enforcement through international agreements. The Cloud Act itself offers the mechanism of the Executive Agreements. Countries such as the United Kingdom and Australia have chosen this path and closed bilateral agreements with the United States, which should enable an accelerated, direct data access under certain conditions. These agreements promise efficiency gains compared to the often slow traditional legal assistance procedures (MLATS). However, other countries or regions, such as the EU, hesitate to conclude such an agreement, among other things because of concerns about compatibility with their own high data protection standards (GDPR, Schrems II). They continue to rely primarily on the established MLAT process, which provides for a stronger integration of the judicial authorities of the requested state, even if it is considered inefficient. The choice between these paths represents a balancing act between efficiency in law enforcement and the protection of fundamental rights and sovereignty.
- Technical and organizational measures (TOMS) by companies: Regardless of state strategies, companies take measures to reduce the risks of the cloud act. This includes the use of strong encryption methods, ideally under the only control of the customer using the cryptographic keys (Bring your own key- byok, hold your own key- Hyok), the careful selection of the storage location (e.g. data center within the EU), the implementation of strict access controls, the use of pseudonymization or Anonymization techniques, cooperation with local partners or system integrators that manage the data on behalf of the customer, or the implementation of hybrid cloud architectures, in which particularly sensitive data remains in your own data center (on-premise).
Case studies: EU, Switzerland, Brazil, China, Russia
The use of these strategies can be illustrated in concrete country examples:
- EU: pursues a multi -track approach. The base forms strong regulation (GDPR, Data Act). Initiatives such as Gaia-X should strengthen sovereignty, but have to fight with challenges. At the same time, negotiations on a cloud act agree with the United States are running, which shows the ambivalence between the claim to the sovereignty and the need for cooperation. The high dependence on US providers remains.
- Switzerland: Your data protection law (REVFADP) has closely based on the GDPR and uses similar mechanisms for international transfers (adequacy resolutions, SCCS). In response to Schrems II, Switzerland implemented its own agreement with the USA (Swiss-US Data Privacy Framework). Nevertheless, the basic risk of the cloud act remains because Swiss companies that use US services are potentially affected.
- Brazil: With the LGPD, a comprehensive data protection law with an extraterritorial effect has created and established an independent data protection authority (ANPD). There are specific rules for international transfers and the use of cloud services, especially in the regulated financial sector. The exact interpretation and enforcement, also with regard to conflicts with laws such as the cloud act, is still under development.
- China: Consistently relies on state control, strict data localization and the promotion of a isolated domestic market that is dominated by national champions. Data protection (in the sense of PIPL) also serves state control and national security.
- Russia: pursues a similar strategy of digital sovereignty through strict data localization, promotion of domestic providers and increasing technological decoupling from the West, reinforced by geopolitical factors.
Technical and organizational measures of companies
For companies that use US cloud services or act globally, the implementation of robust technical and organizational measures is crucial for risk minimization. These include:
- Transparency and risk assessment: Proactive communication with customers via jurisdiction risks and implementation of thorough risk analyzes (Data Transfer Impact Assessment - TIAS) in order to evaluate the sensitivity of the data and the potential effects of access.
- Careful selection of providers: Examination of alternatives to US providers, especially European or local providers who are not subject to the US judiciary. Evaluation of the compliance commitments and security architectures of the providers.
- Encryption and key management: use of strong encryption for data “at Rest” and “in Transit”. Controlling over the cryptographic keys is crucial. Only if the customer manages the keys exclusively (Hyok) can he effectively prevent access by the provider (and thus potentially by US authorities). Solutions in which the provider manages the keys (Bring Your Own Key - Byok can be misleading here), do not offer complete protection. However, it should be noted that data for active processing in the cloud often have to be deciphered in the RAM, which represents a potential access window.
- Access controls and governance: implementation of strict identity and access management (IAM) guidelines to limit the access to data to the absolutely necessary. Examination as to whether access by personnel from certain jurisdictions (e.g. USA) can be prevented technically and organizationally.
- Hybrids and multi-cloud strategies: shift in particularly sensitive data and workloads to a private cloud or on-premise infrastructure, while less critical applications remain in the public cloud. This enables differentiated risk control.
- Legal structuring: In some cases, the foundation of legally separate subsidiaries in various jurisdictions can be considered in order to break through the “control” of the US mother company through data in other regions. However, this is complex and requires careful legal design.
- Reaction to inquiries: Development of clear internal processes for dealing with authorities. This includes examining the legality of the request and the willingness to contest orders if they are in conflict with local laws (e.g. GDPR).
However, it should be noted that technical and organizational measures reach their limits. As long as a company that is subject to the US Jurisdiction, ultimately the “Possession, Custody, Or Control” has the basic legal risk of publication according to the cloud act remains. Even strong encryption can be avoided if the provider can be forced to publish the keys or has access to the management level. A purely technical solution cannot fully eliminate the legal problem of the sovereign claims.
The following table offers a comparative overview of the various national strategies:
Comparison of national strategies to reduce cloud risks
Different countries and regions worldwide have developed different strategic approaches to deal with the risks of the US Cloud Act. The data solocation strategy, such as it is practiced in China, Russia, partly in India and Vietnam, stipulates the strict storage of data in Germany. Although this increases national control and sovereignty and promotes local industry, but often proves to be inefficient, expensive and innovative and limits access to global services.
The EU with the GDPR, Switzerland with the FADP, Brazil with the LGPD and Great Britain with the UK GDPR, on the other hand, focus on strengthening its own regulations with high data protection standards, clear rules for international data transfers and strong supervisory authorities. This strategy protects the rights of the citizens and creates a legal framework for conflict cases, but does not solve the basic jurisdiction conflict directly and burdens companies with high compliance requirements.
Some regions actively promote local providers and digital ecosystems, such as the EU with the GAIA X project or China and Russia with its industrial policy. These measures reduce the dependence on foreign providers and strengthen technological sovereignty, but are often associated with limited competitiveness towards large international providers and have proven to be lengthy and cost -intensive.
Great Britain and Australia have closed executive agreements as part of the cloud act with the USA, while the EU is still in negotiations. These bilateral agreements enable accelerated data access for law enforcement authorities and create legal certainty for providers, but can handle national protection standards and legitimize US access to data.
Many countries implicitly adhere to the traditional MLAT process (Mutual Legal Assistance Treaty), which offers established legal assistance procedures with stronger rule of law, but is considered slow, bureaucratic and ineffective for digital evidence.
Companies worldwide also implement technical and organizational measures such as Hold-Your-down key encryption, strict access controls, hybrid cloud solutions and comprehensive risk analyzes. These measures can reduce risks and demonstrate compliance, but often do not solve the basic legal problem and are complex and potentially costly in implementation.
Suitable for:
A problematic law with far -reaching consequences
The analysis of the US Cloud Act and its global effects reveals a complex network of legal conflicts, technological dependencies, geopolitical tensions and strategic reactions. The law, although with the understandable goal of more efficient criminal prosecution in the digital age, is in its current form proves to be highly problematic and carries considerable risks for individuals, companies and countries worldwide.
Summary of the core problems of the cloud act
The central criticism and problem areas can be summarized as follows:
- Collision with national sovereignty and legal systems: The explicit extraterritorial claim of the Cloud Act, which US authorities granted access to data regardless of the storage location, fundamentally collides with the sovereign understanding of other countries and their legal systems. This becomes particularly clear in the conflict with the EU GDPR, in particular Article 48, which builds on the recognition of foreign authorities.
- Legal uncertainty and “Conflict of Laws”: For global companies, especially cloud providers, the law creates considerable legal uncertainty. They see themselves potentially contradictory legal obligations- on the one hand, on the one hand the US arrangement, on the other hand, on the other hand, the data protection or confidentiality law of the country in which the data are stored or its citizens are affected. This leads to a dilemma with potential sanctions on both sides.
- Erosion of trust: The cloud act considerably undermines confidence in US technology providers. The possibility of access by US authorities, by circumventing local procedures or without the knowledge of those affected, stirs up distrust regarding the security and confidentiality of data. This applies to both personal data and sensitive company information and is reinforced by the parallel concerns about US monitoring laws (Schrems II issues).
- Risks beyond law enforcement: Although the declared purpose is to combat serious crime, there are concerns about misuse of access rights for the purposes of state surveillance or economic espionage. These risks are difficult to control and contribute to the loss of trust.
- Promotion of global fragmentation: The unilateral approach of the cloud act acts as a catalyst for global fragmentation tendencies in digital space. It provokes counter -reactions in the form of data localization laws and the promotion of national digital ecosystems, which encourages “balkanization” of the Internet and hinders free global data flow.
Overview of the global dependency landscape
The analysis of the market shares shows massive global dependence on the three large US cloud hyperscalers AWS, Microsoft Azure and GCP. In North America and Europe in particular, they control over two thirds of the market for cloud infrastructure services. This high concentration creates a wide potential attack area for the cloud act.
In contrast, countries such as China and Russia, which have established largely independent digital ecosystems through strong state regulation, promotion of domestic providers and market shuttle. They demonstrate that less dependency is possible, although often at the price of limited global connectivity and potentially lower freedom of choice.
The European Union is in an ambivalent position: On the one hand, there is a very high factual dependency on US providers, on the other hand there is a strong political will and concrete initiatives (GAIA-X, Data Act) to strengthen digital sovereignty and promote alternatives. However, the success of these efforts is still uncertain.
Outlook on future developments
The trends initiated by the cloud act and similar developments should continue:
- The spread of data localization laws will probably increase, as more and more countries are trying to keep control of data on their territory.
- The efforts to build regional or national cloud alternatives will continue, even if the success in competition with established hyperscalers remains difficult. Initiatives such as Gaia-X could rather develop into standardization framework for data rooms.
- The United States is expected to try to complete further executive agreements with strategic partners in order to facilitate data access. Negotiations with the EU remain complex.
- The legal disputes about international data transfers, in particular in the context of Schrems II and its successor regulations (such as the EU-US Data Privacy Framework), will continue. The question of the “adequate level of protection” in the USA remains virulent.
- For companies, the development and implementation of robust compliance strategies and technical solutions for risk reduction (encryption, hybrid models etc.) is becoming increasingly important in order to be able to act in this complex environment.
In conclusion, it must be recognized that the cloud act addresses a real problem: the need for law enforcement authorities to be able to access evidence that is stored across borders in the digital age. The traditional MLAT methods are often too slow and inefficient. However, every sustainable solution must find a way to reconcile this legitimate need for law enforcement with the fundamental rights to data protection and privacy as well as the sovereignty of the states. The cloud act in its current form does not do justice to this balancing act from the perspective of many international observers and those affected. It represents a US-centered solution that does not adequately take into account the concerns and legal systems of other countries and thus creates more problems than solves. An internationally coordinated solution based on mutual respect for the legal systems and strong fundamental rights guarantees remains an urgent task.
Recommendations for action
The analysis of the cloud act and its global effects result in concrete recommendations for action for European companies and organizations as well as for political decision -makers.
For European companies and organizations:
- Implementation of comprehensive risk analyzes: Companies should systematically evaluate their dependence on US cloud providers. This includes a classification of the processed data based on sensitivity and an analysis of the potential risks in the event of data access by US authorities. The implementation of data transfer consequences (TIAS), as required in the context of Schrems II, is essential.
- Careful selection of cloud providers: It is advisable to check active European or other non-I-American cloud providers as alternatives that are not subject to the US judiciary. Providers should be assessed based on their contractual commitments regarding cloud act requests, their technical protective measures and their compliance certifications.
- Robust contract design: Contracts with cloud providers should contain clear regulations for data processing, the storage locations, safety measures and to deal with authorities, in accordance with Article 28 GDPR.
- Implementation of strong technical measures: The use of end-to-end encryption, in which the cryptographic keys remain exclusively under the control of the customer (Hold Your Own Key-Hyok), is an important protective measure. Strict access controls (identity and access management) and, where sensible, pseudonymization or anonymization techniques should be implemented.
- Use of hybrid or multi-cloud strategies: For particularly sensitive data, the use of private clouds or on-premise infrastructures can be useful, while less critical workloads can remain in the public cloud. This enables differentiated risk control.
- Observing specific legal advice: In view of the complex and constantly developing legal situation, the collection of specialized legal advice on the assessment of the specific risks and the development of a sustainable compliance strategy is essential.
For political decision -makers (especially in the EU):
- Strengthening European digital sovereignty: the consistent promotion of initiatives such as GAIA-X and the support of the structure of competitive European cloud providers are necessary to create real technological alternatives and reduce dependency. The data act should be used to ensure fair market conditions and control over data.
- Clear attitude in international negotiations: In the negotiations on a possible EU-US Cloud Active Agreement, it must be ensured that the high European data protection standards (GDPR, EU fundamental rights charta, requirements from Schrems II) remain without restriction. This includes robust guarantees for the rule of law, proportionality, transparency and effective legal protection for those affected. The priority of established legal assistance procedures (MLATS) or equivalent protective mechanisms should be anchored.
- Promotion of global standards: At the international level, the EU should work for the development of coordinated rules and standards for cross -border data access by authorities based on the rule of law, respect for fundamental rights and mutual respect for national legal systems.
- Education and support for the economy: Political decision-makers and supervisory authorities should provide clear guidelines and practical support for companies to help you evaluate the risks and the implementation of compliance measures in dealing with the cloud act and international data transfers.
We are there for you - advice - planning - implementation - project management
☑️ SME support in strategy, consulting, planning and implementation
☑️ Creation or realignment of the AI strategy
☑️ Pioneer Business Development
I would be happy to serve as your personal advisor.
You can contact me by filling out the contact form below or simply call me on +49 89 89 674 804 (Munich) .
I'm looking forward to our joint project.
Xpert.Digital - Konrad Wolfenstein
Xpert.Digital is a hub for industry with a focus on digitalization, mechanical engineering, logistics/intralogistics and photovoltaics.
With our 360° business development solution, we support well-known companies from new business to after sales.
Market intelligence, smarketing, marketing automation, content development, PR, mail campaigns, personalized social media and lead nurturing are part of our digital tools.
You can find out more at: www.xpert.digital - www.xpert.solar - www.xpert.plus